Making your First Cloud Security Investment?
Before you make your investment, let's learn about cloud security, vendors and overall market.
Quick Sectional Links -
What is Cloud Native Application Protection Platform (CNAPP)?
Why do we need security in the cloud? Shouldn’t AWS/GCP/Azure/OCI provide it natively?
With more and more companies moving their data center from on-prem to cloud, it has increased the importance of cloud security manyfold. Cloud-based solutions have brought numerous advancements in the industry and over the past 5 years, we have seen new vendors eating the pie with exorbitant valuations. Let’s learn more about the underlying technology and why security is important for the cloud. The reason for this blog is not only to cater to the security audience but provide insight to a wider audience including individual & institutional investors, software engineers, product managers, and all other folks who are interested in learning about this space.
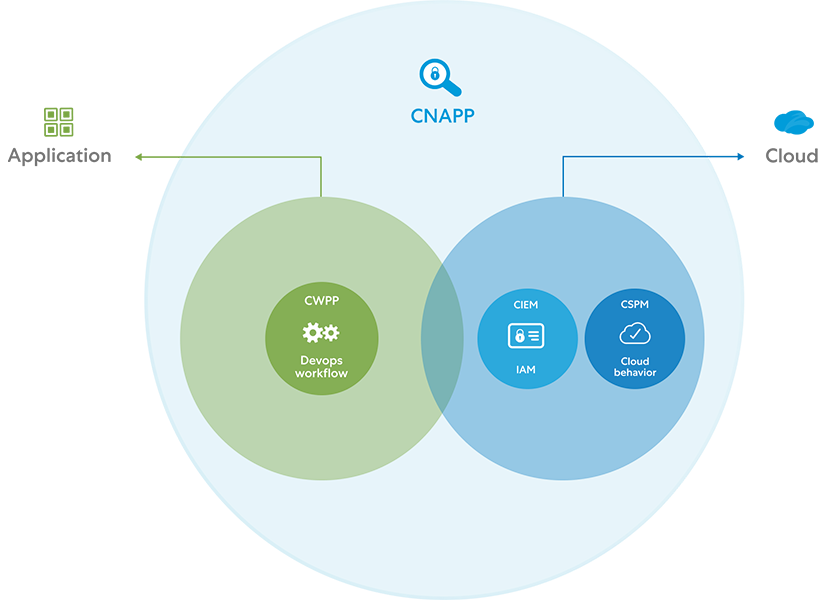
What is Cloud Native Application Protection Platform (CNAPP)?
Gartner coined the term "CNAPP" in 2020 (After coining CSPM, CIEM, CWPP, etc.), and if we go by their own definition -
“CNAPPs consolidate multiple cloud-native security tools and data sources, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlements management and runtime cloud workload protection platforms.”
Simplifying what Gartner wrote - These suites of software are designed to protect cloud-based infrastructure, applications, and data. These will ensure user and device authentication, data and resource access control, and data privacy protection.
Source: Gartner (How to protect your clouds with CSPM, CWPP, CNAPP, and CASB)
Why do we need security in the cloud? Shouldn’t AWS/GCP/Azure/OCI provide it natively?
Let’s understand it via an analogy - When you buy the latest smart lock for your house, the smart lock provider will ensure that their patented ML/AI-based (Yikes!!) smart lock will provide the highest level of security. It’s on the user to configure that smart lock, keep different patterns for different users and monitor the activity of who is entering the house.
For example, if you put 0000 as your password, you can’t really blame the smart lock provider. If you forget to lock the door, it’s on you and not the provider.
Similarly, these cloud vendors (AWS/GCP/Azure/OCI) operate in a shared responsibility model where a cloud service provider is responsible for managing the security of the public cloud while the subscriber of the service is responsible for securing what is in the cloud. Over the years the move to the cloud has brought a wide range of security challenges. There is a huge rise in the usage of cloud resources which has made the environment remarkably complex and difficult to protect.
Why do I care?
The cloud security market is currently valued at $7.8B in 2022 and it is expected to grow at a CAGR of 19.9% to $19.9B by 2027 according to a report published by marketsandmarkets. Doesn’t seem that large right now but with the pace of innovation, offerings and move to cloud computing, it will definitely outpace that CAGR. If you zoom out and see how things are aligned, it is very similar to entering an EDR market in early 2012-13. That makes this entire industry interesting and something to watch out for next couple of years. Here is a small finding from Mckinsey on the total addressable market for the entire cybersecurity suite and how cloud security is still under 5 percent.
Source: Mckinsey (“New survey reveal $2T market opportunity for cybersecurity technology and service providers“)
What are the key components of CNAPP?
Going by the definition, CNAPP provides a more integrated approach that covers the entire app lifecycle from development to runtime protection. With CNAPP, you can uncover vulnerabilities in open source, find cloud misconfigurations, proactively detect threats, remediate in real-time, and tick your sheet with comprehensive compliance, and reporting.
Now that we have covered the what, why, and how parts, let’s talk about a few key components of the CNAPP security suite before we move forward. I wouldn’t be surprised if we have a new cloud security jargon this year and I would have to update this blog but as of now, these are some of the major components -
CSPM - Cloud security posture management identifies and remediates risk by automating visibility, uninterrupted monitoring, threat detection, and remediation workflows to search for misconfigurations across diverse cloud environments/infrastructures. CSPM determines whether all the cloud applications and services are configured and securely correctly.
IaC - Infrastructure as Code provides engineering teams with version control and continuous integration/continuous delivery (CI/CD) to the testing and deployment process. In simple terms, it is helping set up cloud infrastructure in a programming language. Why it’s important? In the old IT days, you would file a ticket with IT to get a server set up, and then after a few days, it is assigned to you. In this modern age, engineers can spin up their instance in a few seconds and whatever you do inside their space is a black box. IaC is all about the process of moving the security to the left i.e. earlier in the application development life cycle.
CWPP - Cloud Workload Protection Platform includes a cloud-native security strategy that is primarily used to secure workloads. The main use case for CWPP is to offer high security to workloads. What are workloads? Cloud-based workloads are applications, services, computing, or capabilities running on cloud resources for example VMs, Containers, Kubernetes, and Serverless.
CIEM - Cloud Infrastructure Entitlement Management technologies discover all identities and users, and their entitlements and enforce identity and access governance controls to reduce excessive entitlements and right-size privilege access across the multi-cloud infrastructure.
CDR - Cloud Detection & Response is relatively a newer term but does the same EDR job for the cloud. CDR gives an edge to security teams to control the visibility in the cloud and detect threats on the cloud in real time.
Let’s look at some big and upcoming players -
Let’s see how these companies are stacked against each other in terms of technology. I don’t think it’s fair to compare the features of company A vs B, I strongly believe it’s more relevant to compare the outcomes of feature A vs B. If you want greater visibility and can compromise on efficiency, maybe you do want an agent-based system. If you want to choose the vendor with the latest eBPF technology (Though you can have an API-based eBPF) but you cannot give up on the efficiency of the machine, maybe it’s not the right approach for the company. In short, not every feature is the end-all-be-all, you need to see how the industry trend is going (as an investor), does it align with your environment (as a buyer), does it provide value for your money, and so and so forth.
For example, not taking a dig but this report from one of the vendors cannot be consumed as is. Why? Customer segments are completely different what works for Customer A with a small environment will not be true for Customer B with a large IT presence. When you compare results from MITRE evaluation, it’s not a good idea to consume them at face value, there are other nuances to think about on how those detections are reported. Shrewd execs and investors take everything into consideration and evaluate all these matrices while investing or buying the product.
The reasons for choosing some of these companies are as follows -
Pure cloud security player (Mostly private players)
Provide all these key components of CNAPP
70% or more YoY growth
There are other notable players who are doing a great job in providing cloud security like Palo Alto Networks, Netskope, Ermetic, Uptycs (XDR + CNAPP), and Snyk (Fugue Acquisition). I have kept them outside of the scope for a head-to-head comparison (again, looking for pure cloud players only with the growth condition) but they do offer great products and something definitely to consider.
History & Financial
Technology Overview
Source: Data is sourced from Crunchbase, Pitchbook, Growjo, Gartner, Wiz, Orca, Aqua, Lacework, Sysdig
We have seen these numbers pop up for other B2B businesses but for a security company (Wiz) to achieve astronomical growth (100M ARR in 18 months) is a little odd. What did Wiz do differently?
In my opinion, there are a couple of reasons for their growth, they already had a strong team and had sold their first company to Microsoft for a reported $250M. The same team built the Microsoft Azure cloud security group to $1.5B revenue machine. Of course, a strong team doesn’t always guarantee success but what made them different was great technology. They are agentless, which makes it easier for companies to migrate and in their own terms “Wiz can be rolled out in minutes via an agentless, API-centered approach to seamlessly scan workloads and give organizations full visibility of their cloud environment.“ Wiz analyses the entire security environment via a graph database and it surfaces prioritized risks for development teams to fix. This gives an edge in faster processing as there are no complex joins to find the relationship between different entities. In simple terms, it is easier & faster to analyze the relationship between your container A and user A. Graphdb is useful in analyzing and setting the relationship between nodes & edges with anomalous behavior being all about nodes and edges. Aqua, Orca, Lacework, and Sysdig have come up with or plan to offer similar graph-based technology, so we will see how they align their offerings for the next few quarters.
Again, this is not an in-depth review for these company’s technologies and financials, this is just a brief introduction about them. If you want a detailed review, feel free to reach out separately.
How to find the right value?
You can go through the above metric and list down some of the key points for these companies and do your own due diligence. In this market, where the buzz is only around FCF, it is definitely not possible for these above-mentioned companies as they are still in the early phase. One of the key metrics that you can think of for cloud security companies apart from a solid founding team is to look for 2.5-3x YoY ARR growth, 110-130% net dollar retention, healthy gross margin (50-70%), and a good NPS score.
Again, please do your due diligence and look for other factors too.
Good Danger Zone?
Cloud is a beast when it comes to the attack surface, it's difficult to monitor with the amount of noise and hard to write behavior-based detections. However, cloud is one part of the entire attack chain, it could be a misconfigured container but it wouldn't be difficult for an attack to not move to endpoints to get more data from an executive's laptop and acquire more surface-level data. These vendors are solid in terms of cloud coverage and provide immediate ROI but the key for any security vendor is to cover all the bases. It’s difficult to predict anything but if history is any indication, if you only operate in your niche market and reduce your pace of innovation, there will be a new player to replace/fight you in the next 24-48 months. In contrast, look at how PANW 0.00%↑ aged really well and started with a firewall as their core offering. In the last 5 years, while they were crushing the competitors ( FTNT 0.00%↑ & CHKP 0.00%↑), they saw a plateau of growth and ventured into other security areas, acquired companies and became leaders in a few, and ate a decent market share in all the core security businesses (Firewall/ZTNA, SASE, XDR, SOAR, CNAPP).
Vendors like CRWD 0.00%↑ , S 0.00%↑, PANW 0.00%↑ have already made a move to observability space with their offering of Logscale, Scalyr (acquisition), and Cortex Data Lake.
Under pressure to innovate quickly! Who will be the winner?
In my opinion, all cloud security vendors operate in their own niche and can definitely thrive for a few more years. In order to fight in this market, Wiz/Orca/Aqua/Lacework/Sysdig need to produce cloud security innovations at an incredible pace or they will be consumed by a more unified vendor. The user persona for these products is simple and we should also think about making these platforms easy to use. If you have built the next-generation AI engine but an analyst cannot use it, it is probably of no use. It’s a tough market to survive and with security unification, it would be important to show the value and stack the offerings against bigger players ( CRWD 0.00%↑ , S 0.00%↑ , DDOG 0.00%↑ & PANW 0.00%↑ ) to produce a good fight or being acquired by the "bravo's" of the world.
Security Unification - method to integrate multiple security technologies into a single framework. There is definitely a tradeoff when it comes to unification, either you lose on the quality or you lose on time navigating between different vendors. Any company that can bridge the gap (tough to offer everything out there), will get a bigger piece of the pie for the next few years.
Hot Take!!
There could be an opportunity for companies like Tines, Swimlane, or a new vendor to make security software more relevant. If they make the right pitch and put more emphasis on how specialized software (PANW for firewall, CRWD for XDR, Wiz for Cloud, Symantec for DLP) is the only way to go, they can definitely squeeze in there and eat some market (TAM is small but it is meaningful). Their job would be to consolidate alerts, make sense of them, perform supervised and unsupervised learning, do additional filtering, and provide a prioritized list to the analysts.
I have tried to keep the blog as simple as it can get so that when you give your next CNBC interview or talk to your friends about security, you don’t react like Mark Minervini.
Disclaimer: I am not a financial adviser and neither this article should drift your choice to invest in one company over the other. Details listed on the blog are just for informational purposes, and shouldn’t be taken as investment advice and I do have investments in some of the companies mentioned here.








This is such an amazing post. Loved the details. Great work :)