XDR Wars: Who Holds the Key?
SentinelOne, CrowdStrike, and Palo Alto Networks Face Off in a Market Showdown
Important: Before proceeding to read this post, please take a moment to read and understand the disclaimer at the end of the post.
Quick Sectional Links
The cybersecurity industry has undergone substantial changes in recent years, primarily due to the rise of sophisticated cyber attacks and threat actors. Consequently, security technologies, including Extended Detection and Response (XDR), have evolved from conventional products like EDR, EPP, and antivirus solutions. Organizations are bolstering their security defenses by moving to a more comprehensive solution. In this post, we will be covering the why, what and how of XDR and talk about three major cybersecurity companies, namely CrowdStrike (CRWD 0.00%↑ ), SentinelOne (S 0.00%↑), and Palo Alto Networks (PANW 0.00%↑). In this post I tried to cover all three major vendors and highlight the positives of one over the other.
Additionally, this blog aims to delve into the features and benefits of these XDR solutions, as well as their distinct approaches to threat detection, response, and remediation. We will also explore how XDR fits into the broader cybersecurity landscape and why it is increasingly becoming a crucial tool for organizations seeking to proactively manage evolving threats.
XDR is an endpoint solution that combines advanced threat detection, comprehensive visibility, and coordinated response across multiple security layers, providing a holistic defense against sophisticated cyber threats that may span across endpoints, networks, cloud environments, and now applications. With its unified and proactive approach, XDR empowers organizations to detect, investigate, and mitigate cyber threats in real-time, providing a more resilient and adaptive defense against ever-evolving cyber threats. Here is a quick recap on how the industry evolved over the last few decades -
How does an XDR work?
I’ll try to explain it via analogy (If it doesn’t work for you, I apologies), imagine you are at Meta’s Menlo Park office. You might have seen the number of buildings and each building has its own physical security guard. In addition, there is a central location from where all the physical security activity is monitored and they have their response team working from that central location. Whenever someone enters any building, that building’s security guard will ask the visitor their name, reason, place, etc. all this information is sent to the central security office for further processing. In this case, each individual guard is monitoring the entire building and sends all the information to a centralized location.
Similarly, these XDR agents are individual security guards for the building sitting on individual hosts (laptop, server, cloud instance) and collect the telemetry of the machine and send it to a centralized cloud for processing.
This picture by Florian Roth perfectly summarizes the current state of XDR but I do see more use cases for XDR. I’ll cover those use cases in the technical section of this post.
Source - What is XDR by Palo Alto Networks?
Nir Zuk, founder and CTO of PANW 0.00%↑ coined the "XDR" term during their Ignite'18 user conference and this image by PANW 0.00%↑ is just an overview of XDR architecture . When we talk about the entire attack chain, endpoint is just one piece in the puzzle. A mature system would help the analyst understand the larger picture and hence the artifacts from other sources like network, cloud, apps and other data source would only complement the current detection & response. "X" in XDR stands for extended which translates to “everything” that can be ingested to a data lake and used to perform analysis on that data in a central location.
Why do you need an XDR?
XDR is an essential tool for organizations for several reasons. XDR solutions offer endpoint visibility, enabling real-time monitoring and analysis of endpoint behavior, which is crucial for identifying anomalies and threats. XDR solutions provide detailed information about threats and suspicious activities, which helps organizations investigate and remediate threats quickly. While XDR can be a valuable tool in enhancing an organization's cybersecurity posture and improving its ability to detect and respond to threats, it may not be a specific compliance requirement in and of itself. However, implementing effective cybersecurity measures, including XDR capabilities, can help organizations meet their compliance obligations by providing better visibility into potential security incidents, facilitating timely response, and mitigating potential impacts of security breaches.
Why do I care?
According to research from Ponemon Institute, approximately 70% of all breaches occurs from an endpoint. This is an interesting statistic as it highlights the importance of endpoint security layer and, more importantly, underlines the attack surface that endpoints presents. According to Verified Market Research, the global endpoint security market is expected to grow at a CAGR of roughly 7.87%, from $13.43B in 2020 to $24.7B by 2028.
Source - Verified Market Research - Endpoint Security Market Size And Forecast
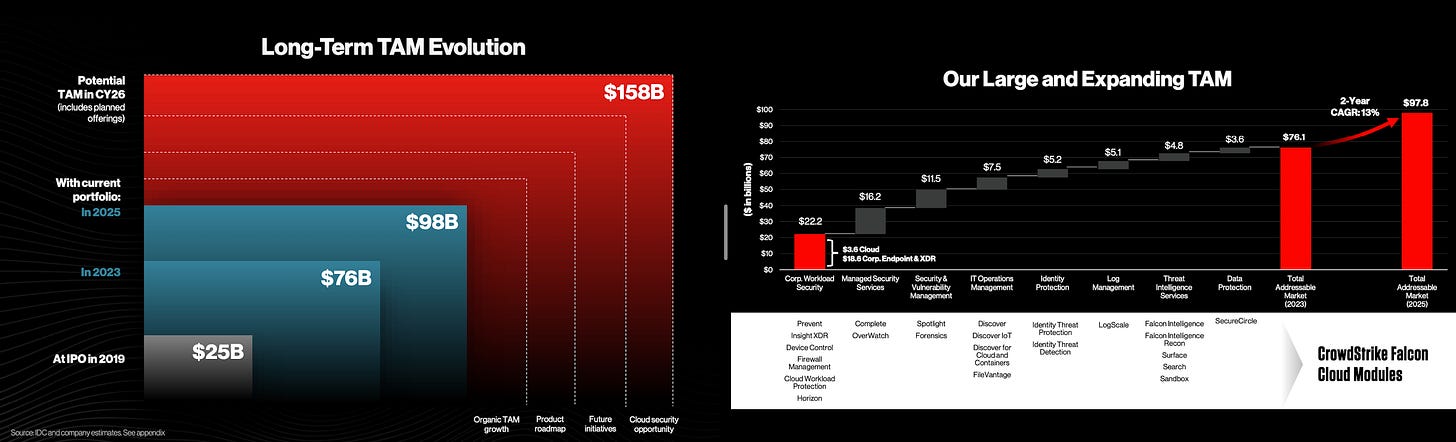
TAM (Total Addressable Market) for these vendors is much more as they do offer different module and claim to have different TAM for each module. Some of the modules are Threat Intelligence, Vulnerability Management, and Identity Management and others and they always try to present themselves as a platform for security and not just endpoint security. Here are some TAM reports shared by CrowdStrike in their investor presentation -
Source - CrowdStrike Investor Presentation
Let’s look at some of the major players
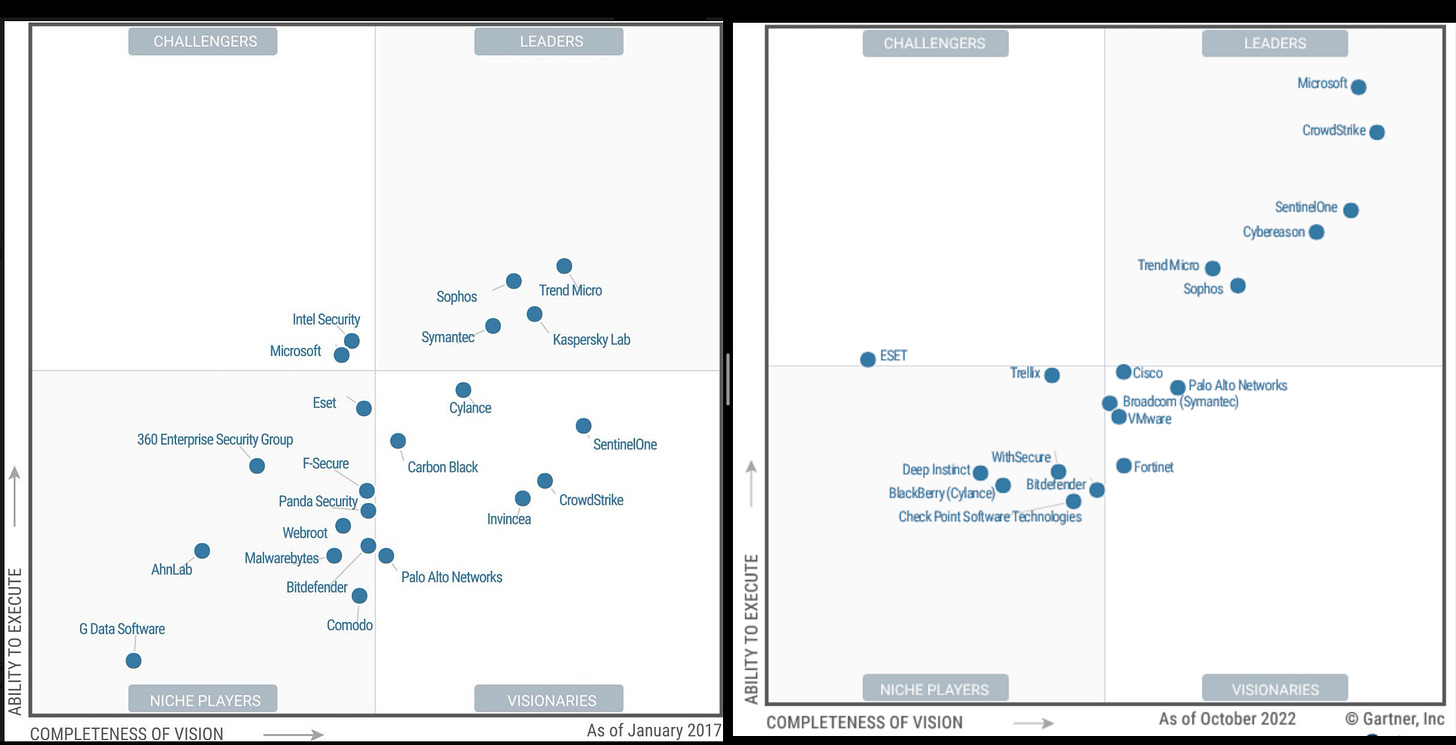
Endpoint security is set to experience new challenges with ever-changing demands from enterprises. You can see from the image how quickly the industry changed; look at Gartner's magic quadrant from 2017.
Source - Gartner, Left - Gartner’s magic quadrant 2017, Right - Gartner’s magic quadrant 2022
This field is poised for even more risk, innovation and significant market shifts in the next few years. Therefore, vendors need to adapt to changed demands and threat landscape and keep innovating with incremental progress. Like other security areas, endpoint security has quite a few vendors. However, some major vendors in endpoint space are PANW 0.00, CRWD 0.00, $S, MSFT 0.00, Trend Micro ($TMICY), McAfee, Sophos, VMW 0.00 , Cybereason, BitDefender and some newer players like Cynet, Confluera (Acquired by XM Security). It makes a cogent argument to include all of them in the comparison; however, I have listed down three major players based on several reasons like market vision, features, positioning, leadership, revenue growth, customer count for XDR and 2022 Gartner's magic quadrant.
You might wonder why PANW 0.00%↑ is included with comparatively low MQ rating (2022)?
PANW 0.00 is one complete vendor with all the pieces in place, and that too with solid execution. You look at the network, cloud and SOAR functionalities; it does make life easier for the end users. Additionally, they have solid innovation, research and leadership teams, and I'd bet my bottom dollar on them to eat a good market share from incumbent players like Cybereason (looking for a buyer), Trend Micro and VMW 0.00.
An ideal strategy for PANW 0.00%↑ would be to compete with CRWD 0.00 and S 0.00 (As S 0.00%↑ AND CRWD 0.00%↑ are still working on consolidation and PANW 0.00%↑ is way ahead) but target the organization they can beat left, right and centre and simultaneously improve their current portfolio. CRWD 0.00 and S 0.00 are architecturally stable and more polished products in terms of XDR. It would be good to target customers who are in their renewal cycle and can't go with the incumbents due to the rising sophisticated attacks.
Technology
Pricing
SentinelOne: SentinelOne offers a flat rate for their endpoint security solution, which includes all features and functionalities. The pricing is based on the number of endpoints protected, with discounts available for longer-term contracts.
CrowdStrike: CrowdStrike offers tiered pricing based on the number of endpoints protected and the level of support required. They have multiple packages, and you can choose from the standard Falcon Prevent package or the complete Falcon Prevent package.
Palo Alto Network: Palo Alto Network offers a variety of pricing models for their endpoint security solution. The pricing is based on the number of endpoints protected and also offers a consumption-based pricing model.
GTM Strategy
SentinelOne: For years, SentinelOne has prioritized a partner-friendly approach in its go-to-market strategy, particularly with strategic partnerships like MSSPs. To enhance these relationships, they have developed capabilities such as multi-tenancy, automation, and role-based access control. Additionally, they are expanding their relationships from MSSPs to VARs (Value Added Resellers) and VADs (Value Added Distributors) across the world.
SentinelOne also recognizes the importance of the cloud in its go-to-market strategy and has seen significant customer interest in its cloud offerings and Wiz partnership. The company views cloud and endpoint sales as complementary and has had success with standalone cloud deals. By treating its endpoint and cloud businesses as competitive advantages, SentinelOne plans to continue growing across all these different vectors.
CrowdStrike: CrowdStrike's go-to-market strategy revolves around utilizing its technology and establishing strategic partnerships to extend its market coverage. Initially, the company aimed at the large enterprise sector and promoted the Falcon platform to such organizations, which delivers an extensive array of endpoint protection, threat intelligence, and response services. To reach out to the SMB market, CrowdStrike developed Falcon Go, a lightweight package designed exclusively for SMBs. Moreover, the company is exploiting its strategic association with Dell to provide the Falcon platform to Dell's customers worldwide. This partnership allows CrowdStrike to access a wider market, including small to medium-sized businesses, via various channels, such as traditional resell agreements on devices sold through Dell's direct sales team and as the cornerstone of Dell's managed cybersecurity services offerings.
Palo Alto Networks: For the last few years, Palo Alto’s strategy is to acquire innovative technology companies and integrate their products into their offerings. They focus on smaller to mid-sized acquisitions in the product category and utilize the expertise of the acquired companies' founders to drive growth. They have been successful with this approach and have developed a unique go-to-market approach. Additionally, they are focused on enhancing their go-to-market capabilities, particularly in cloud and Cortex total market capabilities and are working on product enhancements in XDR space. This will definitely give them confidence in opening up a large total addressable market in future quarters.
Customers
SentinelOne: In their fiscal fourth quarter 2023, SentinelOne gained approximately 750 customers, resulting in a year-over-year increase of around 50%, with the total number of customers reaching north of 10,000. Among some customers, SentinelOne closed a multi year eight-figure deal in Q3’23 which was the largest since inception.
CrowdStrike: CrowdStrike has a strong customer base and a steady growth in their numbers. They recently added 6,694 net new customers for the fiscal year and now the total count is 23,000+ paid customers. CrowdStrike also serves 556 of the Global 2000, 271 of the Fortune 500 and 15 of the top 20 U.S. banks. They also added an 8-figure net new ARR deal to their revenue last quarter. They are also the second fastest company to $2B ARR just behind Zoom communications (Covid Play).
Palo Alto Networks: Palo Alto Networks has close to 4500 customers for their Cortex platform and they also added multiple high 7-figure deals over the last quarter. They are also trying to pilot XSIAM (In simple terms, a SOC platform!) with few customers and trying to bundle it with XDR. Customers can only opt for XSIAM if they have XDR, so the company is attempting to upsell customers to purchase XSIAM due to its features and consolidation play, with the aim of generating more revenue by offering a bundled package to customers.
Acquisitions
SentinelOne: In 2019, SentinelOne acquired Scalyr, a log management and analysis platform, which was aimed at enhancing their cybersecurity solutions. In March 2022, SentinelOne announced the acquisition of Attivo Networks, a leading identity security and lateral movement protection company. Attivo Networks was a leader in Identity based prevention, detection, and response capabilities.
CrowdStrike: CrowdStrike made several acquisitions to enhance its capabilities. This includes the acquisitions of Humio, a log management and observability technology provider, and Preempt Security, a zero trust and conditional access technology provider. In September 2022, CrowdStrike acquired Reposify that provides an external attack surface management (EASM) platform that scans the internet for exposed assets of an organization to detect and eliminate risk from vulnerable and unknown assets.
Palo Alto Networks: Palo Alto Networks has made several acquisitions, including an Israel-based company named Secdo in 2018, which brings sophisticated EDR capabilities, including unique data collection and visualization. Later, they completed the acquisition of Demisto for Security Orchestration, Automation, and Response (SOAR) technology, PureSec for serverless security, Twistlock for container security, Zingbox for Internet of Things (IoT) security, Aporeto for Zero Trust Network Security, CloudGenix for SD-WAN technology, and Expanse for attack surface management. Additionally, Palo Alto Networks also acquired RedLock, a cloud security analytics company, in 2018 to strengthen its cloud security offerings. In 2020, they completed the acquisition of The Crypsis Group, a leading incident response, risk management, and digital forensics consulting firm. In February 2021, they acquired Bridgecrew, a developer-focused cloud security company and creator of the tool Chekov, and in December 2022, Palo Alto completed the acquisition of Cider Security, a leader in application security (AppSec) and software supply chain.
Financials
SentinelOne :
CrowdStrike :
Palo Alto Networks :
Summary :
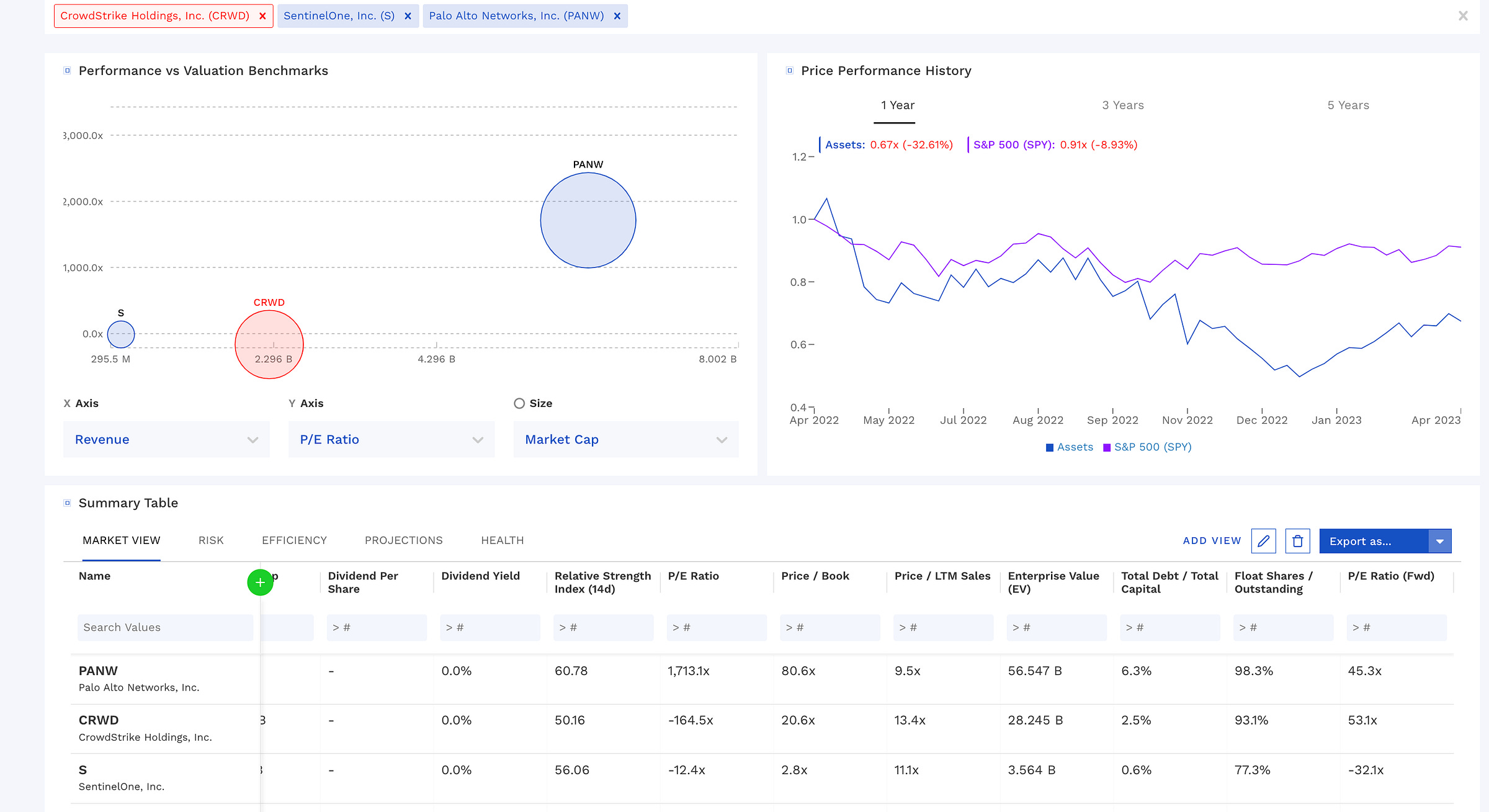
Source - Charts from Finbox
Innovator’s Dilemma
One of the most critical challenges for the security industry is the innovation dilemma. You might remember a time when we had Avira, Avast, McAfee, FireEye, and a couple of others. These are great companies built for ages but they share a similar pain of innovation. Although, some of the companies were sold at a good sum, they had a great opportunity to be a part of this market.
Why can’t these companies disrupt themselves?
You take IBM 0.00%↑ as an example, they had the finest mainframe computer, disrupted by DELL 0.00%↑ laptops, DELL 0.00%↑ ruled the market and was the talk of the town before being disrupted by AAPL 0.00%↑, apple ruled the market with the launch of iPhone and Samsung started their phone offerings with android OS and captured a great share and so on and so forth.
The point is that there is always an external company that reads the market better than these incumbent exceptional companies. The problem is when you keep listening to your existing customers, you keep improving what you already have.
They are still innovating but only to improve the existing product(s). When small becomes big and you are spinning out of the growth stage, introducing processes, and bureaucracy, and adding more checks, you find yourself in a rabbit hole where it’s hard to move the building blocks. Therefore, it’s essential to zoom out and see how to remain small when you are big, how to stay nimble just as you were a startup and operate like UBER 0.00%↑ (Yes, I’m biased), ABNB 0.00%↑, NFLX 0.00%↑ , etc. and disrupt your own company and reinvent yourself before a disruption from an external one.
CrowdStrike vs SentinelOne
I have watched nearly all the public interviews featuring George Kurtz and Tomer Weingarten, and I must say they are exceptional leaders who have built outstanding companies. I have also spoken to several people from S 0.00%↑ and read countless reviews praising Tomer's leadership, which is indisputable. I still believe that S 0.00%↑ has an edge when it comes to the ecosystem. Having a background from Israel and IDF, with the camaraderie in the security community, they have a unique advantage in leveraging partnerships and opening more channels for cross-selling and upselling. Have the cashed in well? Not really, till now I don't feel industry has the same feeling about the technology behind the product. They still need to prove and communicate well the investors and buyers. The recent exclusive partnership with Wiz highlights their focus on making the software more stable, as many of their existing offerings overlap with Wiz. This partnership is beneficial for both S 0.00%↑ and Wiz, as they are likely to face strong headwinds from increased competition in their respective spaces (XDR and CNAPP). While the recent departure of two executives has made headlines, I believe that $S has made some great hires recently, and the new leadership will steer the company to greater heights (you can get an org chart from here).
On the other hand, CrowdStrike has a strong distribution and marketing strategy led by George Kurtz and his team. CrowdStrike positions itself as a one-stop-shop for protecting against nation-state attacks, which is a powerful marketing message that resonates well with the security audience and investors (From CrowdStrike Recent Investor Call - “They hear George on the radio, they watch on TV, they know CrowdStrike”). In some cases, companies are reluctant to switch from CrowdStrike, as the saying goes, "if it ain't broke, don't fix it." The software is packaged well and easy for analysts to understand, making it a popular choice for many. There is enough space for the market to have both these vendors thrive for the next decade.
Can we see a new player in XDR?
It can be argued that the XDR market is saturated with strong market players, making it difficult for newcomers to enter. Nonetheless, I strongly believe that true XDR players are rare and distinguishable by their clear vision and capabilities. Success in this market depends on a solid team, a good product, and strong partnerships, which can help a new vendor gradually acquire market share. While there is room for new players with superior technology and strong market differentiators, such differentiation must be robust, as the migration process is critical for every business. No business would want to spend more money and, more importantly, a significant amount of time migrating to an average or mediocre XDR solution.
Hot Take!
It has been interesting to observe how the XDR industry has evolved over the past few years. With customers demanding more consolidated vendors, it would be challenging to establish dominance and capture the market share from these three vendors. Among the three, S 0.00%↑ boasts the most sophisticated and superior technology, and with an EV/Sales ratio of approximately 8.8x, it appears to be undervalued in my opinion. However, recent departures and headwinds from longer sales cycles and IT spending cuts make it intriguing to monitor price movements in the next two quarters. Despite high marketing spend, they have struggled to convert campaigns into a compelling narrative. On the other hand, CRWD 0.00%↑ has effectively leveraged partnerships, recording top-tier revenue through its partners. They have also established themselves as one of the most successful AWS ISV partners for Amazon. With their new partnerships, such as with Dell, and new SMB opportunities, they present an exciting investment prospect. PANW 0.00%↑'s advantage lies in its large customer base and ability to upsell enterprise customers on XDR & XSIAM offerings. They are miles ahead in terms of being a platform security company with solid integrations with most of the vendors. In my view, these three vendors will continue to dominate the market for the next 3-5 years as customers demand more consolidated and efficient solutions. We are likely to witness more acquisitions and exclusive partnerships aimed at maintaining a competitive edge in the market. The decision to opt for superior technology, a better go-to-market strategy, or a larger market opportunity rests with the investors or the buyers.
As always, if you want the “meat” of the blog and need more in-depth information, feel free to reach out separately.
Disclaimer : The information provided by Security & Markets ("we," "us," or "our") on https://securityandmarkets.com/ (the "site") is for general informational purposes only. All information on the site is provided in good faith; however, we make no representation or warranty of any kind, express or implied, regarding the accuracy, adequacy, validity, reliability, availability, or completeness of any information on the site. The information published on this post is based on publicly available information obtained from online websites, quarterly reports, and resource documentations posted online. The author of this blog clarifies that there is no relationship or affiliation of the author's current or previous employer(s) with this blog. Under no circumstances shall we have any liability to you for any loss or damage of any kind incurred as a result of the use of the site or reliance on any information provided on the site. Your use of the site and your reliance on any information on the site is solely at your own risk. We recommend independently verifying any information obtained from the site before making any decisions or taking any actions based on it. By using the site, you acknowledge and accept this disclaimer and agree to use the information provided at your own risk.











This was so insightful, especially for someone like me who has some experience working in the security field, but with knowledge and expertise that is limited.
Wow - I've never spent this amount of time reading a report.....very insightful. Excellent coverage. (Don't suppose you do the same coverage for the best thrash-metal bands?;-))